Currently, one of the key features of the digital information has been its protection, because many vulnerabilities and attacks are known, and every day, new ones are discovered.
This way, keeping a company’s computational structure updated and protected from vulnerabilities is a detailed job.
In order to assist with this task, vulnerability analysis tools that automate and help track these vulnerabilities may be used.
This article compares two of these popular tools, OpenVAS & Nessus. Continue reading to know the difference between their architecture and know the pros and cons.
OpenVAS has a client-server architecture, in which on the server-side, all the processing is done in search of vulnerabilities, and storage of settings and scans is also performed.
The client-side provides an interface for the network administrator to configure the scan and view your reports.
Network Vulnerability Tests (NVT) are security tests developed in the Nessus’ scripting language, Nessus Attack Scripting Language (NASL).
These tests are available daily through the OpenVAS service NVT Feed which is accessed by the OpenVAS-NVT-sync program.
OpenVAS can be used to find vulnerabilities without knowing how to look for them, as OpenVAS attempts numerous attacks collected from various sources.
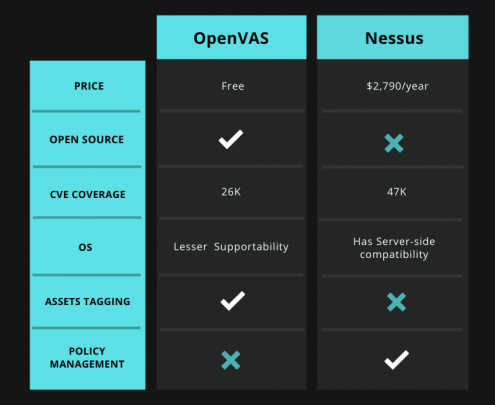
- OpenVAS is a free open-source vulnerability assessment tool that is maintained by Greenbone Networks.
- Common vulnerabilities and exposure (CVE) coverage of around 26,000
- Popular and useful among SME’s
- Built to be an all-in-one scanner
- The scan engine of OpenVAS is updated on a regular basis
- Greenbone provides thorough tutorials for the usage of this tool
- Covers fewer CVEs as compared to Nessus
- Less operating system supportability
- Does not offer policy management
Also Discover: List of 5 Open Source Vulnerability Scanner Tools
Nessus is one of the most popular analysis software of vulnerability. Developed by Tenable, Nessus had its code open until 2005. As of 2008, its license was modified creating a commercial version.
Compared to other vulnerability scanners, Nessus has the distinction of being based on a client-server architecture and being compatible with Windows and Linux as well.
In addition, Nessus stores and manages all of its security vulnerabilities through a system of plugins. The security team can use it to scan its network in order to prevent intrusions and denials of service.
The vulnerability scan, done by Nessus also uses programs written in NASL - Nessus Attack Scripting Language - known as plugins. Currently, the vulnerability scanner has more than 50,000 plugins.
- Common Vulnerabilities and Exposures (CVE) Coverage of around 47,000
- Great customer support
- Facilitates group testing
- Offers real-time visibility
- Nessus has server-side compatibility with operating systems
- Built-in scan templates
- Nessus costs around $2,790/year & is not viable for smaller companies
- It does not allow checking the local security policies of remote systems
- Network overload can be a drawback for Nessus
- Does not offer asset tagging and risk management
OpenVAS vs. Nessus: Tabular Comparison
Concluding Words
OpenVAS and Nessus, each one of the tools have its own share of advantages and disadvantages.
With the utilization of both the software, it is possible to increase information security by fixing vulnerabilities before they are exploited by attackers.
As future work, it is possible to carry out a detailed analysis for each CVE found by the software.



0 Comments